A zero day virus is a brand, new virus that has just been released to the public, and for which there is not yet any information or antivirus protection. This is the story of how our team encountered and identified a new Cryptolocker variant, and then raced the clock to prevent its spread and data loss.
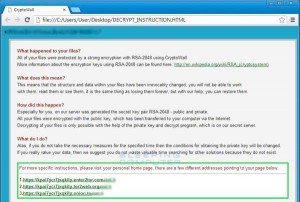
Last week a client called in stating that their server was filled with files with the extension .ECC. This was an extension that we had never seen before, so it immediately flagged us of a potential threat.
According to our research, .ECC files are associated with DVDisaster — an application created by a developer named Carsten Gnörlich. This didn’t really make any sense; we doubted our clients were using this new application. And even if they were, why would the application create .ECC files on their file server? We couldn’t figure it out.
Unless…!
Suddenly we realized we were dealing with a virus. We began scanning their file server with our antivirus and malware tools. But our tools came up empty. What gives?
Still playing on our virus-hunch, we decided to bring one of the .ECC files into our test environment. Carefully, we opened it up.
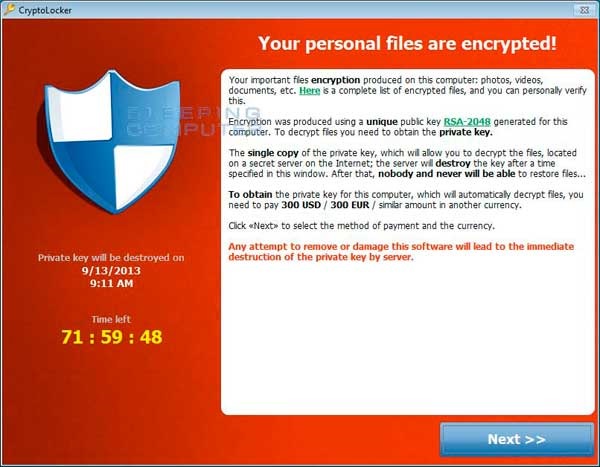
And there it was: a variant of Cryptolocker, in all of its terrible glory.
Our client’s network was infected.
We scoured the Internet but couldn’t find anyone, anywhere, who had seen this Cryptolocker variant. Not only were we dealing with a vicious form of ransomware, but, we realized, we were dealing with a zero day virus. There was no antivirus for it yet, because it was brand-new.
Our team has had extensive experience in dealing with Cryptolocker in the past, so we had a baseline for this virus’s potential behavior. Cryptolocker will first encrypt users’ own hard drive and then try to encrypt mapped network drives. We immediately began looking for a host machine.
A host machine is the machine that introduced the virus into the network.
Once you locate the culprit, you can choose to wipe Cryptolocker with your AV or Malware tools from the infected machine. In this case, for precaution, we decided to pack up the machine and wipe the hard drive completely. Cryptolocker has a nasty habit of encrypting files and hiding them on the hard drive. Being that this was a zero day infection, we were not sure if this variant left any malicious files on the server — or anywhere else.
In past versions of Cryptolocker, once you found and killed the host machine, you could delete the files. (They are pretty much useless without the encryption key, and the files themselves are not malicious.) But since we weren’t sure, we decided to use our Microsoft partner account to reach out to the WOLF team.
WOLF is the team at Microsoft that is dedicated to security, vulnerabilities, and virus/malware removal. They are essentially the software world’s version of Navy SEALS. They are fantastic. We called them up, and, like a true black ops team, they jumped in with their custom-built tool and scanned the server and the network, looking for any traces of the virus left behind.
The WOLF team was able to determine that the .ECC files were merely encrypted, and no further infection existed. They were also able to determine how the virus came into the network and what vulnerabilities caused this.
We patched machines to keep them secure, and we also recommended that users do the following:
- Ensure your antivirus is up to date and properly scanning.
- We recommend installing a complimentary malware scan in addition to the antivirus scan. (We recommended Malwarebytes Pro.)
- Install AdBlock Plus for all Internet browsers. This helps block unwanted ads and can potentially protect them from anything trying to get through as well. For information on AdBlock Plus for Chrome, click here.
With good, current backups, patching of your Windows and 3rd party applications, and these steps above, I believe this can help any company stay safe out in the cloud without compromising any employee freedom to go where they choose.
For more information about Cryptolocker, or any security issues, feel free to call our engineers at Everon at 1-888-244-1748.