CAUTION: Some of the following steps are above the level of beginners. If you are unsure about anything you read here, please call us at Everon (888-244-1748) and we can help you through it.
Sooner or later everyone receives an email that looks legitimate, but you have a feeling it could be a scam or a virus waiting to attack. Here are a few examples of questionable emails:
- From someone you know, but off topic.
- From a Company/Vendor warning of a problem with your account.
- Announcing you have a voicemail/fax waiting for you.
- Official-looking email from your bank requesting you to login.
It is always a difficult choice. If this is a legitimate email I need to follow through, but if it is a hoax it can cause a lot of problems I don’t need right now. What to do…?
First, do not open the any attachments or click on any links in the email. Now, if your Company has any procedures in place to address questionable emails, follow the recommended steps. Otherwise I recommend that you contact the sender and question the email.
- From an individual: create a new email to them expressing your concern.
- From a known Company/Vendor: call them and question the email.
- From a new/unknown source, notify you supervisor – do not open, do not click inside the email, and do not forward.
- From a Company/Bank regarding a personal matter: call them or login to the site AS YOU NORMALLY WOULD – do not use the link in the email.
I know, I know, none of this is new to you. That being the case, let’s take a questionable email and break it down.
NOTE: It is important you are familiar with the Windows feature “Hovering.” When you place the mouse over an object WITHOUT CLICKING, a popup will show you additional details. This is known as Hovering. Do not click when Hovering, as this will initiate the code associated with the object.
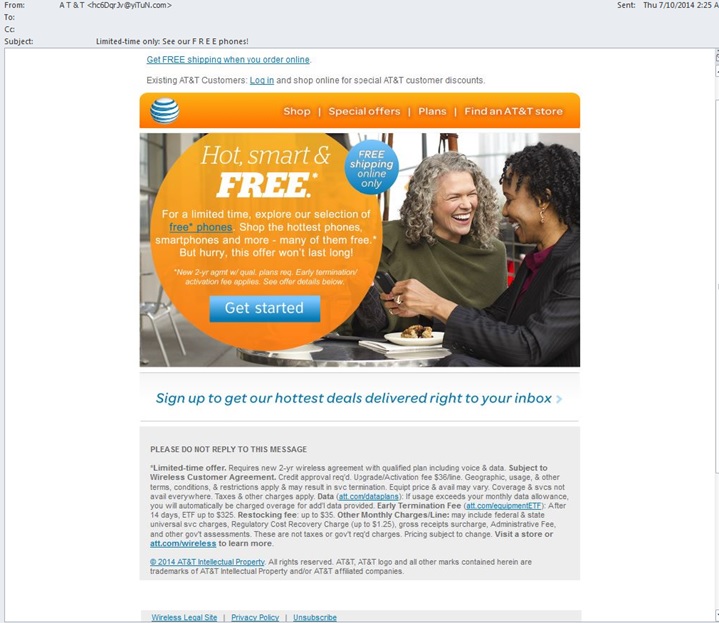
Here is an email I recently received in my Hotmail account. At first glance everything seems okay. But let’s take a closer look at a few problems:
Wrong “From” email address
At the top of this email you can see that “From” is A T & T <hc6DqrJv.yiTuN.com>. Because I have configured my email to display both the label and actual address, I can see the actual email address.
You may only see the A T & T if you received this email. In that case, just hover over the A T & T and the popup will show you <hc6DqrJv.yiTuN.com>.
When you send an email, you can display your name in the “From” field (instead of displaying your email address). This is a very common and useful feature, but in this case it is being used to hide things from you. So now we know this is not really from AT&T but from some cryptic email address. This alone is enough to let you know to just delete this email.
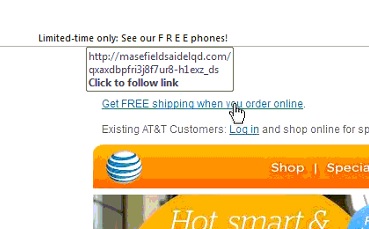
Embedded links do not take you to AT&T
Now let’s take a look at the actual email. Really, everything looks fine: a known AT&T image, standard formatting and wording – nothing to lead you to believe this is a scam. That is, nothing until you hover over the links.
The hover-text tells us that if we click on this link we will NOT be sent to an AT&T website. We will end up at http://masefieldsaidelqd…. All the links in this email go to the same location. Again, this alone is enough to let you know to just delete this email.
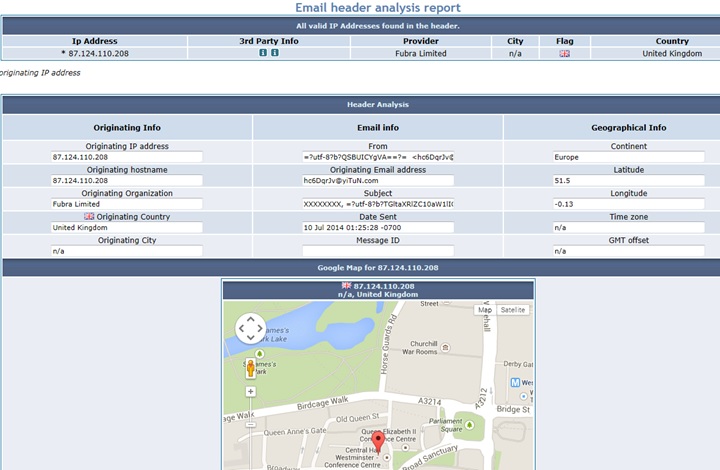
Email Header Analyzer
Every email that is sent has embedded information that describes the path it took from the sender to you. This is called the Email Header and it’s not very easy to read. Here is the actual Email Header for our sample.
x-store-info:4r51+eLowCe79NzwdU2kR3P+ctWZsO+J
Authentication-Results: hotmail.com; spf=pass (sender IP is 87.124.110.208)
[email protected]; dkim=none header.d=yiTuN.com; x-hmca=none
[email protected]
X-SID-PRA: [email protected]
X-AUTH-Result: NONE
X-SID-Result: NONE
X-Message-Status: n:n
X-Message-Delivery: Vj0xLjE7dXM9MDtsPTA7YT0wO0Q9MjtHRD0yO1NDTD02
X-Message-Info:
c21WZ1hAltI9DuizMAEE2QECpxSZUGZG4j2P0KvnFQ5Oq/wSiAiPSbOCWW7QmZMDONMEcOBjWMXYV9Dk2G3eyZRiTxZAdBpO5E1Xr5SqiAWdiuxGlA3k5kj+R//OvPfE4Jw5jOmv8EAwIUCNmc79xJKcP4737N1Q+CskaetIvY9RRY9PhyoYAHA+325kAM7Fj2b6LXibNlbSbtyWUAyW2QNDR/0bZpc
Received: from lzZGq2WEGeQ.com ([87.124.110.208]) by COL004-MC3F55.hotmail.com with Microsoft SMTPSVC(7.5.7601.22712);
Thu, 10 Jul 2014 01:25:28 -0700
From: =?utf-8?b?QSBUICYgVA==?= <[email protected]>
Message-ID: <[email protected]>
Subject: XXXXXXXX, =?utf-8?b?TGltaXRlZC10aW1lIG9ubHk6IFNlZSBvdXIgRiBSIEUgRSBwaG9uZXMh?=
Reply-To: <[email protected]>
MIME-Version: 1.0
Content-Type: text/html; charset=”utf-8″
Content-Transfer-Encoding: 7bit
Bcc:
Return-Path: [email protected]
X-OriginalArrivalTime: 10 Jul 2014 08:25:28.0568 (UTC) FILETIME=[81AB7780:01CF9C18]
Date: 10 Jul 2014 01:25:28 -0700
That’s a lot of very obscure data. But don’t worry, there are free online tools that will break this down for you. One of my favorites is http://www.iptrackeronline.com/email-header-analysis.php. Just paste the header into the box and press submit header for analysis. Scroll down and you will see the following:
Very interesting, the email originated from somewhere in the United Kingdom. Once more, this alone is enough to let you know to just delete this email.
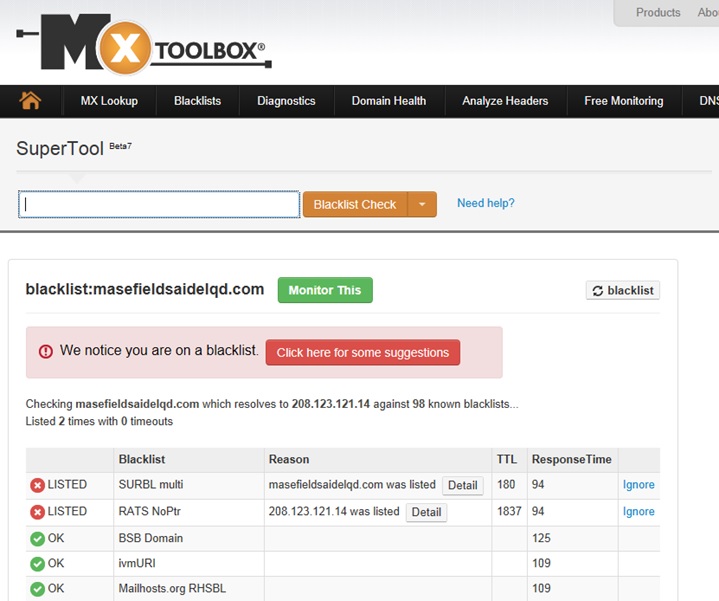
Blacklisted Domains and URLs
If you are still not sure, you can use another free service call Blacklist check. One of my favorites is http://mxtoolbox.com/blacklists.aspx (which also has an Email header Analyzer). Just enter the first part of the email address we got from hovering (http://masefieldsaidelqd.com/) and press Blacklist Check.
No surprise, the address is blacklisted (identified as a known source of spam and malicious emails). So now we have more than enough evidence to delete the email and notify our supervisor.
Always keep in mind that the best thing to do is alert you supervisor and / or your IT team immediately when you suspect you have a malicious email. It is always better to be safe than sorry.