In this TechTip, I want to address an interesting quirk we discovered in a client’s O365 hybrid implementation back in September. During the process of migrating all of the mailboxes to the cloud, the decision was made to leave the Public Folders on their on-premises Exchange 2010 server. While the migration was going, we discovered that there was a small subset of those migrated mailboxes that couldn’t access or expand the public folder structure. When attempted, they were presented with the following error in Outlook:
In this TechTip, I want to address an interesting quirk we discovered in a client’s O365 hybrid implementation back in September. During the process of migrating all of the mailboxes to the cloud, the decision was made to leave the Public Folders on their on-premises Exchange 2010 server. While the migration was going, we discovered that there was a small subset of those migrated mailboxes that couldn’t access or expand the public folder structure. When attempted, they were presented with the following error in Outlook:
Cannot expand the folder. Microsoft Exchange is not available. Either there are network problems or the Exchange server is down for maintenance.
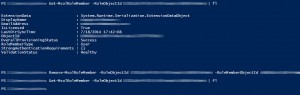
I was able to recreate this same issue on my computer for an account that works fine, as well as for the non-working user. After an exorbitant amount of netsh tracing, Outlook logging, permission verification on the 365 and on-prem sides of the wire, we discovered that there’s an account attribute that get used in the authentication process back to the on-prem Exchange box. It’s called LinkedMasterAccount.
Evidently in a hybrid environment, if this attribute is populated, authentication against an on-prem Exchange server’s public folders will fail with that vague error message I mentioned above. The solution here is a fairly quick and easy one - clear the attribute from the AD account.
In the on-prem Exchange server, fire up the Exchange Management Shell, and run the following Powershell command: Set-User -Identity [email protected] -LinkedMasterAccount $null Once that’s been run, force a FULL DirSync to run, close Outlook, and try again.
And remember, you can always contact us at [email protected], or reach us at 888-244-1748, for help. We’re available 24/7!