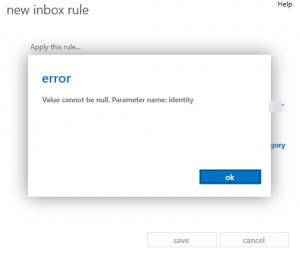
In this TechTip, I want to address a potential fix for an error message we’ve come across when creating a rule in Office 365 that encrypts email messages. Encryption in O365 leverages a Microsoft service called “Information Rights Management,” or IRM. This is supposed to be an enabled/provisioned feature for an Enterprise (read: E3) tenant when it’s created, but as we’re all painfully aware, not all of these automatic provisioning things happen as they’re supposed to. That having been said, if you’re trying to create encryption rules in 365 and run into the following error, chances are that IRM isn’t completely/properly enabled and you’ll have to do it manually through Powershell:
You can't create a rule containing the ApplyOME or RemoveOME action because IRM licensing is disabled.
Should you see this, log into MOP as a global admin, and from Service Settings -> Rights Management -> Manage make sure that Rights Management is active. Once done (and making the assumption that you are in North America), connect to Powershell as a global administrator, and run the following commands:
Set-IRMConfiguration -RMSOnlineKeySharingLocation “https://sp-rms.na.aadrm.com/TenantManagement/ServicePartner.svc”
Import-RMSTrustedPublishingDomain -RMSOnline -name "RMS Online"
Test-IRMConfiguration -RMSOnline
Set-IRMConfiguration -InternalLicensingEnabled $true
The third command (Test-IRMConfiguration) should come back with an overall result of PASS. If it does not, you will not be able to run the fourth. If you hit a FAIL during the test, contact your 365 support folks. We’re advised that this can take up to 24 hours to take effect. I’ve seen it apply as quickly as within a few minutes, but if not, wait the obligatory full day before raising hell. ![]()