Keeping track of IT assets is important for any business. It helps you know what you have and who is using it. It can also be an overwhelming and a time intensive task which causes it to be put on the back burner for many. Honestly, just finding and selecting a solution that fits your business needs can take a lot of effort.
There are several ways to go about keeping track of your assets: from a simple spreadsheet to a specialized software that tracks via bar codes. Usually the more features there are the more money you pay, which doesn’t always make sense for a small business. Manually managing a spreadsheet is cumbersome and can easily become out of date, but specialized solutions can be overkill and expensive.
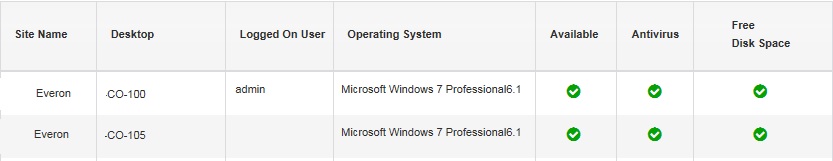
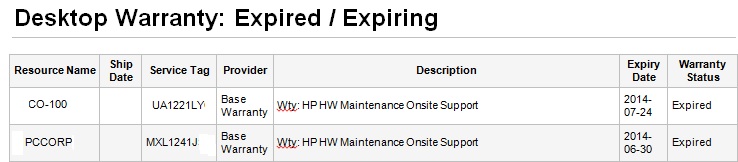
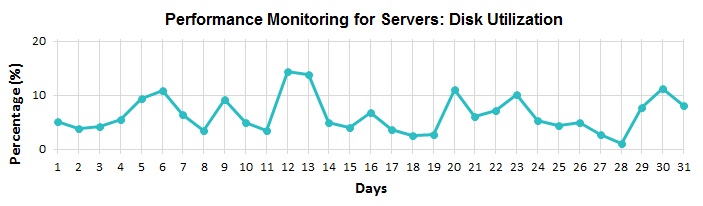
Another option is a software agent that is installed on your workstations and servers. It only takes a moment to do and ties back into a management portal. One of the biggest advantages of this solution is the technical data and reporting that can be generated quickly; something bar code or spreadsheet systems can’t do. Want to know what computers have expired warranties? Which ones have an old version of Windows? This is invaluable when budgeting for IT expenditures and coming up with a proactive replacement plan. Or from a performance standpoint, review trends to better optimize your equipment.
Beyond the asset tracking and reporting functions, another key feature is proactive alerting of issues like low disk space, outdated antivirus, or stopped system services to name a few.
The examples above is just a taste of the what the tool can do and is one of the many things Everon can offer when supporting your IT needs. Give us a call today at 888-244-1748. We can help implement this tool for your business!