For many technicians, reusing a computer is part of the job. We have taken many computers, formatted the hard drives, re-installed OSes, and re-purposed the machines for other uses.
Did you know that when you reformat a hard drive through the standard Windows methods (i.e. deleting the partition during your Windows 7/Windows 8 install), you actually leave behind traces of your old OS? Reformatting a drive does not get rid of all of the data. In order to do that, you want to overwrite any existing data present with 0s (technical term referring to binary code).
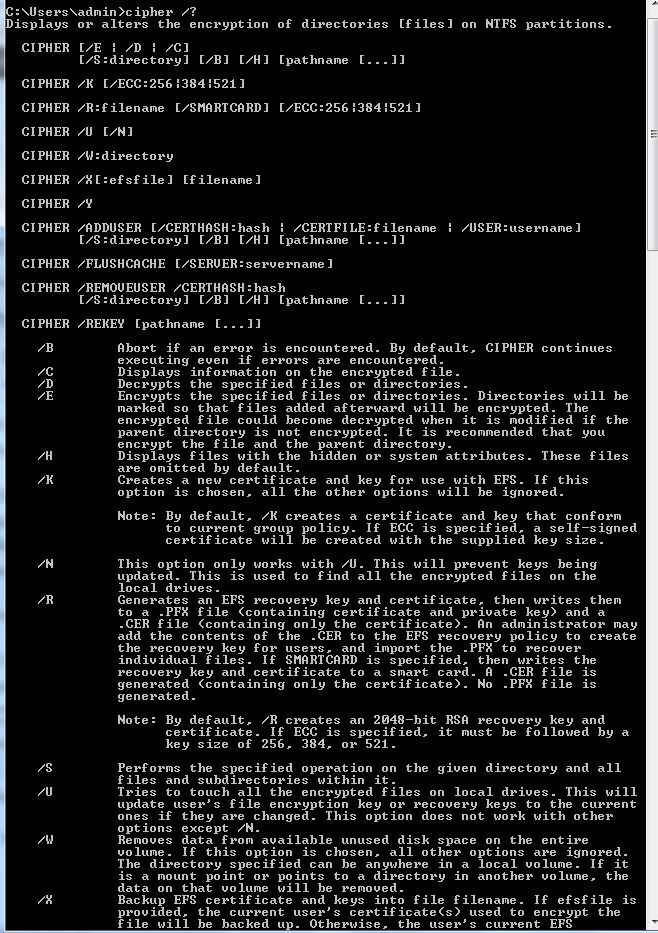
How is this possible? Windows actually has a pretty cool built-in tool for handling this, called cipher.exe.
Cipher was built to encrypt and decrypt files and folders, but it can be used to overwrite data as well. Simply put, in order to securely overwrite your partition with 0s, open a CMD prompt and type: cipher /w:{drive letter}:
You can actually overwrite individual folders as well, just by adding the folder name onto the cipher CMD, like this: cipher /w:{drive letter}:\{folder name}
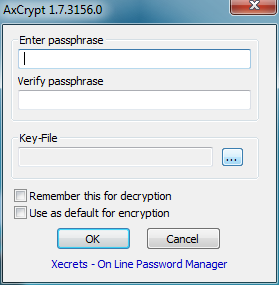
You can also encrypt files by using the CMD: cipher /e (files and folders that are later added to this option will also be encrypted)
And, of course, you can decrypt files by using the CMD: cipher /d (same as above, any files and folders added later are decrypted by default)
For a complete list of commands, type cipher /?
As with anything, really, this tool will make it a lot harder to recover any data that might have been on the hard drive. However, it is never a guarantee. Virtually anything can be recovered on a hard drive. Forensic companies use write-blocking devices approved by the Department of Defense, but that equipment is very expensive, and usually only in the hands of the good guys. Cipher.exe will protect you against most low-level bad guys looking to recover potentially harmful data off of your hard drive.