I use a Mac and a PC at my job, and one thing we fall victim to, if we do not lock our computer when we walk away, is we end up coming back to a desktop wallpaper of David Hasselhoff.
So we are always told to lock our PCs. Fortunately, this is easy to do. You simply press the Windows key + L and it locks your machine (The Windows key is the key between ctrl and alt, that has the Windows flag on it).
But I also needed to find a way to lock my Mac — which isn’t as easy as the nice, two-key combo Microsoft has laid out for us.
You can lock a Mac through key combinations. In newer Macs, you can click control + shift + the power button, and you will see your screen go black, and if you tap any key on the keyboard, it will wake up the screen, and you can see that your Mac is locked.
However, in my case, I can’t even reach my power button, so this just won’t work. What I do (and I consider this the best and easiest way to lock a Mac) is to lock by using Keychain Access.
Keychain Access is the equivalent of Windows Credential Manager, in that it saves passwords that you frequently use on the Mac. In order to use Keychain Access for locking your Mac, you will, of course, need to set a password on your Mac (otherwise what’s the point in locking, if users can hit ‘return’ and go right into your Mac).
To set a password on a Mac, click on the Apple logo in the upper left-hand corner of the Mac, and go to System Preferences. From there you will see a location called Users & Groups.
Inside Users & Groups, you will see your account listed. You might have to click on the lock, down in the lower left-hand corner, to make changes (if you do, it will require a password, and if you have none set, you can simply click OK). Once you have the ability to edit your account, click on it. You will see the location, next to your photo, that states Reset Password. This is where you will enter your password.
You can then click the lock to prevent further changes and move on to Keychain Access.
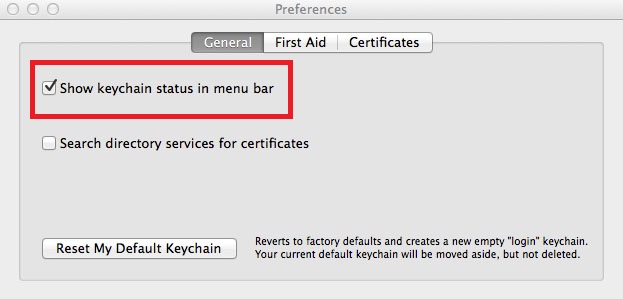
When you launch Keychain Access, you won’t need to do anything in the window that pops up, only in the Preferences for Keychain Access. To access Preferences, click on the words “Keychain Access” in the upper left-hand corner, and go to Preferences…
In Preferences, under the General tab, put a check mark where it states: Show keychain status in menu bar
This adds an unlocked lock in the menu bar in the upper right hand corner of your Mac. If you now click on that icon, you have an option to ‘Lock Screen’.
It’s as simple as that!