When Microsoft released Windows 8 they were targeting the tablet population. So naturally, with a tablet, they have built in some pretty neat tricks with hand gestures. One of the coolest tricks introduced is the addition of picture passwords.
In the past, when locking a machine, you would have to use a standard keyboard password that included letters, numbers, symbols, or any combination of those. With Windows 8 you can now choose a Picture Password. What this means is that you choose a picture, draw up to three gestures on the picture, and this will unlock your machine.
To turn on this feature, go to “Sign-In Options” under the Users tab (found under Change PC Settings). There will be an option for “Create a Picture Password.”
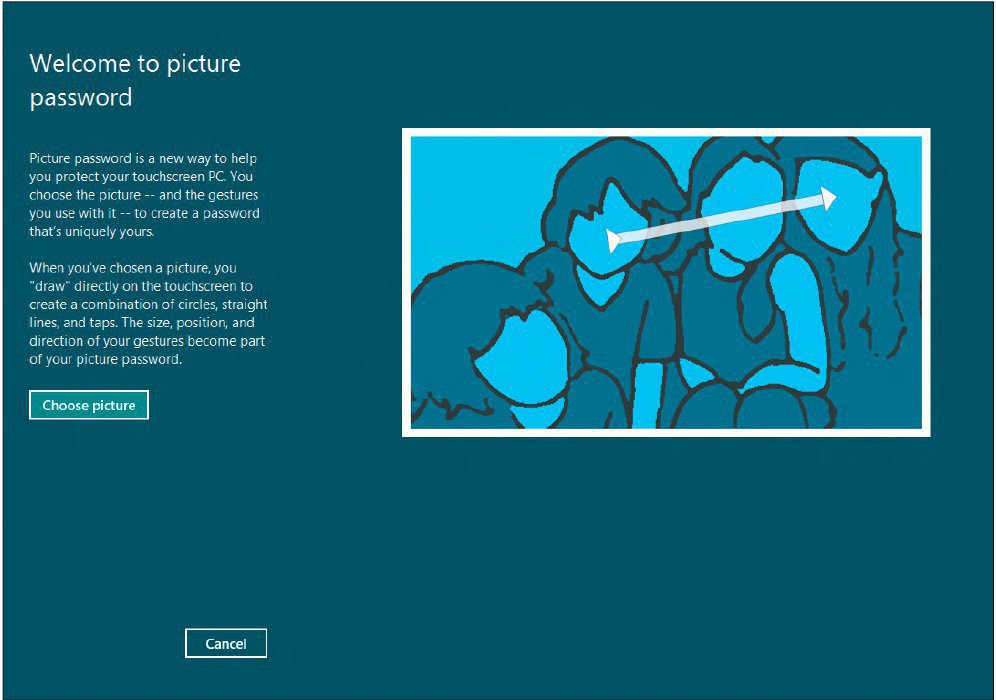 You are limited to what gestures you can put onto your picture. They can only be circles, lines, or taps. When logging in, you will have to use the same three gestures in the same three areas on the picture to get into the machine. But otherwise, it’s as simple as that.
You are limited to what gestures you can put onto your picture. They can only be circles, lines, or taps. When logging in, you will have to use the same three gestures in the same three areas on the picture to get into the machine. But otherwise, it’s as simple as that.
One thing to note: researchers at Arizona State University and Delaware State University believe this method of authentication can be cracked rather easily. You can read about their study here. Consider that when creating your picture password. (To understand how secure passwords are and how easily they can be cracked, check out my previous blog post detailing that information here. While the picture password option is a very neat idea, and can work in safe, internal situations, nothing beats the standard text password.)
To understand all of your options, and see some cool tips and tricks for Windows 8, feel free to reach out to our engineers at Everon: 1-888-244-1748. We’re here for you 24/7, 365.