There is yet another storm brewing where mobile left off, with a new world called “The Internet of Things” (IoT). Twenty-six billion new devices will be connected to the Internet by 2020 (Gartner Group). IoT homes, known as smarthomes, or Connect Homes, are, and will be, the first adopters of these new devices. Small businesses will be the second.
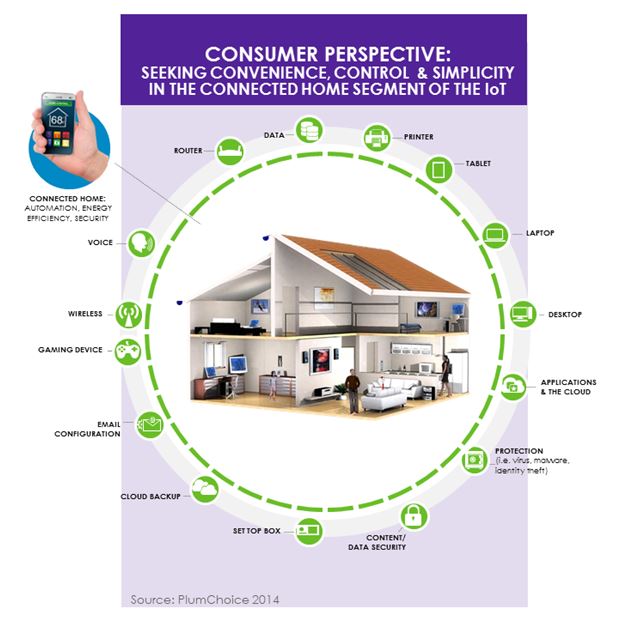 Small business owners are also home owners, many of whom will try out new IoT devices in their homes. The decision process is much quicker for SMBs, and if decision makers like what they see, they can quickly translate, implement, and deploy new things in the workplace.
Small business owners are also home owners, many of whom will try out new IoT devices in their homes. The decision process is much quicker for SMBs, and if decision makers like what they see, they can quickly translate, implement, and deploy new things in the workplace.
In order to gain a “second mover benefit,” however, you need to know what technologies will migrate from home to business. You also need to understand which ones will provide a high ROI (return on investment).
The top two types of devices on which SMB owners should educate themselves – and implement in their homes as a trial – are energy and security devices. Ten percent of US households with broadband have at least one smart device with energy-related functions, including eight percent with a smart thermostat and six percent with smart lighting (Parks Associates, Feb 2015). Canary is one of the first smarthome security devices ($249 USD). It tracks motion, temperature and vibrations. http://canary.is/ SMB will move faster than enterprise companies, and they will have an immediate, positive ROI by implementing solutions which reduce energy consumption and increase security.
To further learn which technologies are best suited for both your home and business, look at solutions that address these key areas: smart thermostats, smart locks, smart light bulbs, smart smoke detectors, smart energy management devices, smart alarms, surveillance IP cameras, and smart hubs. You should note that some solutions are still in their infancy, but manufacturers have already begun to identify vital opportunities to improve both product and business continuity.
Then, regardless of the device you select to migrate to your business, after evaluating your potential ROI, it’s important to examine the security risk of exposing more of your network and critical data to yet another device that is linked to the Cloud. Work with your managed service provider or internal IT department to assess the exposure. An experienced tech team, like Everon, can ensure you have the best protections in place to be able to safely implement home solutions in your small business.
——-
You may also like:
- Turning Your Cell Phone into a Wireless Hotspot
- Top 7 Wireless Security Habits You Should Have for Your Home Network
- Can Your TV Steal Your Information?
- Winter Storm Juno: What to do when you have to work remotely
- Turn your old smartphone into a webcam!
- Now Offering Webroot Antivirus