What this means to you
As a trusted IT adviser, one of our jobs is to constantly evaluate new technologies that come our way. After reviewing Webroot SecureAnywhere Antivirus endpoint protection software, we are confident it will be the best solution for many of our customers.
Webroot offers a revolutionary, cloud-based Antivirus technology that protects against advanced security threats in real-time. According to PCMagazine, “Webroot joins Bitdefender and Kaspersky as Editors’ Choice for commercial antivirus.”
What you need to know
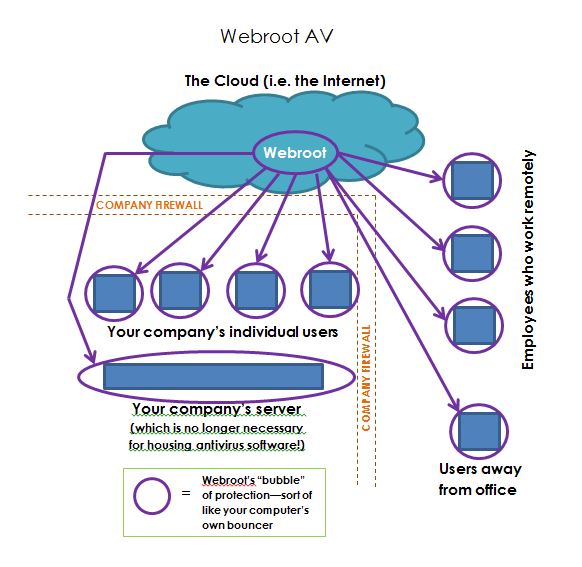
 Webroot provides full remote user/endpoint management via cloud-based management console. Because it is cloud-based, there is no on-site-management hardware or software to operate or maintain.
Webroot provides full remote user/endpoint management via cloud-based management console. Because it is cloud-based, there is no on-site-management hardware or software to operate or maintain.
Webroot also provides real-time threat detection. It can proactively protect against new security threats as they’re detected – sort of like your own, personal bouncer standing right outside your computer. While it requires an Internet connection, its offline mode protects the user against potential infections from removable media (CD/DVD, USB, etc.). It does this by taking a snapshot of the current computer configuration and then watching for any changes made to the system while the user is offline – especially changes that are typical of malicious software behavior.
Webroot also offers automated monitoring, roll-back, and infection remediation for the highest efficiency. In the MRG Effitas 360 Full Spectrum test, which measured a software’s time to detect an infection, Webroot was noted as being one of three solutions able to remediate a computer either on or before the first user reboot. Scan times are also dramatically reduced by logging only newly-introduced software and scanning only that software.
Is this solution ideal for you?
After the initial full system scan, additional scans typically take only 26 seconds compared to the industry average of close to 10 minutes. (This is according to the PassMark Software Performance Benchmark Testing, which gave Webroot an overall score of 97 out of 104. The second place software was a distant 70.)
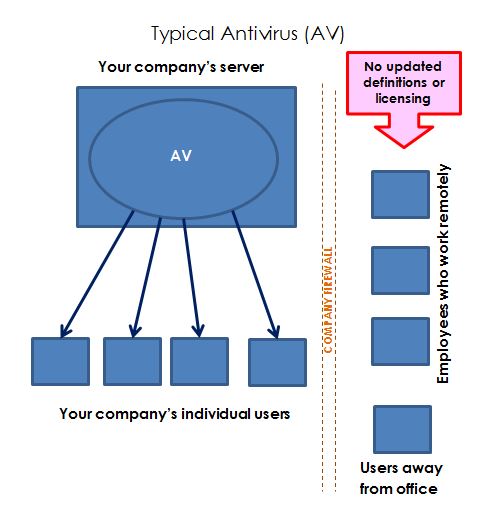
Historically, the installation of an antivirus came with limitations that the user had to accept in order to get some level of protection. An antivirus could not be deployed in tandem with another antivirus, as these caused conflicts. Typical antivirus software also required a server console in order to adequately manage all workstations within a business.
Webroot alleviates the need for a server console by allowing full management of clients through the web-based console. It can be installed alongside other software because of its ability to heuristically scan for infections both on and offline. This is an ideal solution for companies with employees in remote locations, who don’t have direct access to a console server, or who have no server at all. This also means that license renewal is no longer a tedious, manual process for those workstations. Everything is managed directly through the web console and our installed monitoring software.
What should you do next?
So you’re interested in Webroot? If you are a current Everon customer, please feel free to contact your account manager to discuss whether this solution fits your current environment and needs. Not an Everon customer? No problem. Everon offers a remote IT department equipped to fully manage your small business’ technology needs. Please call us at 888-244-1748, or email us at [email protected].



