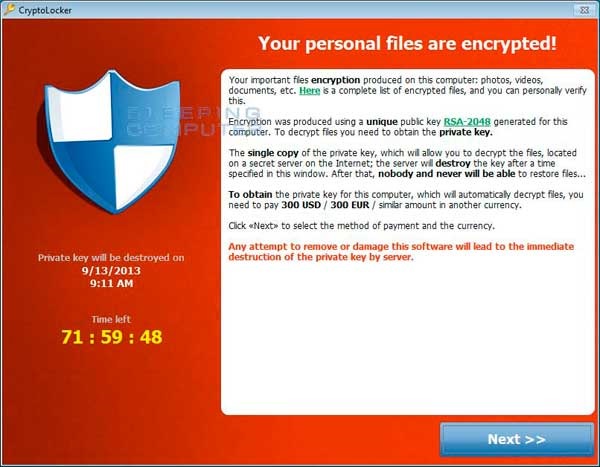
It has been over 9 months since CryptoLocker started encrypting systems and demanding a ransom. In most cases, when a new threat starts attacking computers, a fix or patch that will effectively nullify the threat is released within weeks. It is estimated that over $40 million dollars have been paid to the hackers so far, with no end in sight.
CryptoLocker is currently accepting payments via Bitcoin and MoneyPak. Since bitcoins are not regulated, it is impossible to trace anything beyond into which account the coins were deposited. As for MoneyPak, it is basically an international prepaid card into which people (in this case, victims) can transfer funds.
Is there any way I can protect myself?
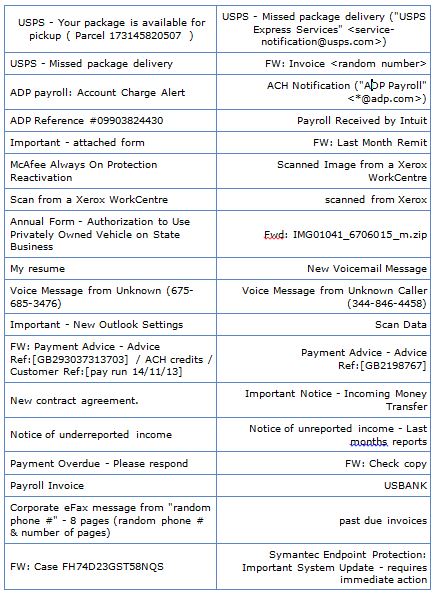
Currently, the most common infection method is via email. Here is a list of some of the emails subject lines used to trick the user into opening the message.
By opening the email, the user is effectively granting permission for the virus to install.
There are a few things that will help prevent infection and minimize its impact:
- Prevent applications that exist in the known location from running. This works because most applications that are downloaded from the internet are stored in common locations. This will not only prevent CryptoLocker from running, it will also prevent you from running any application you download, good or bad.
- Do not open attachments, in any email, that seem out of place or suspicious. This is a good rule of thumb in general, but it is not a complete method of prevention. This is because they are very clever in getting you to believe the email is valid.
- Backup, Backup, Backup. Although sometimes you can get your files back via Shadow Copies, this is not always available — and is being circumvented in later releases of CryptoLocker. By backing up your files and storing them offline, you will only lose data since that last, good backup. (This also means that you should keep several older versions of files in case you accidentally backup encrypted files.)
One important note: CryptoLocker will ONLY encrypt files on drives (local and mapped network). This means if you do not have a drive letter for it, it will not be encrypted. In technical terms, CryptoLocker cannot follow UNC paths.
Like most viruses, it is only a matter of time before a reliable method to block, remove, or decrypt files is discovered and made available. It is taking longer-than-your-average-virus-time to “crack” ransomware. But sooner or later it will be cracked.