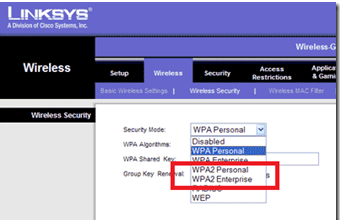
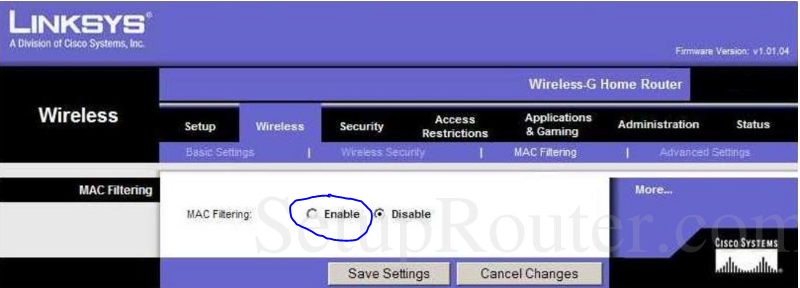
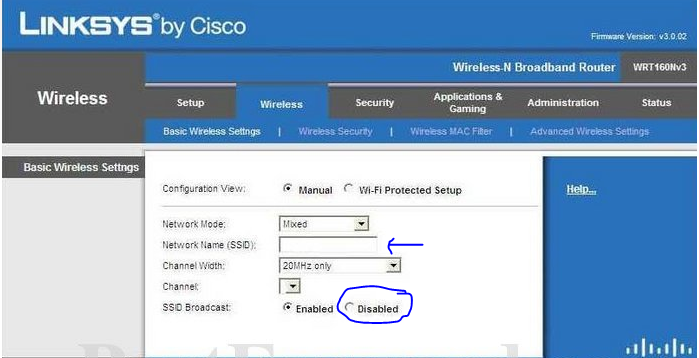
There are all kinds of security threats to a company’s network, and while no security is foolproof, there are things you can do to help maintain your network’s integrity.
To protect individual computers, you should disable a computer’s ability to automatically install new USB drives. This prevents malicious software from instantly loading when a device is plugged in. However, this will only affect the new devices from being installed. Your keyboards and mice will still work.
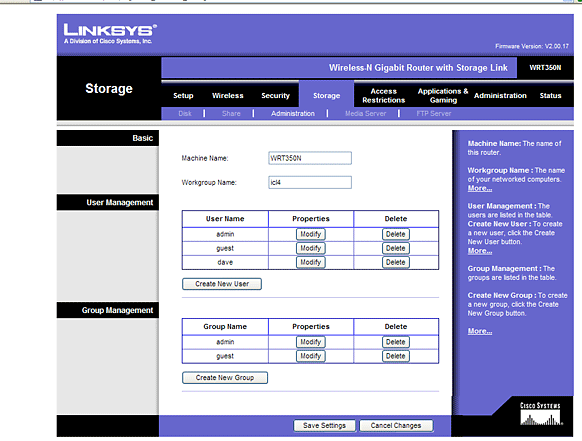
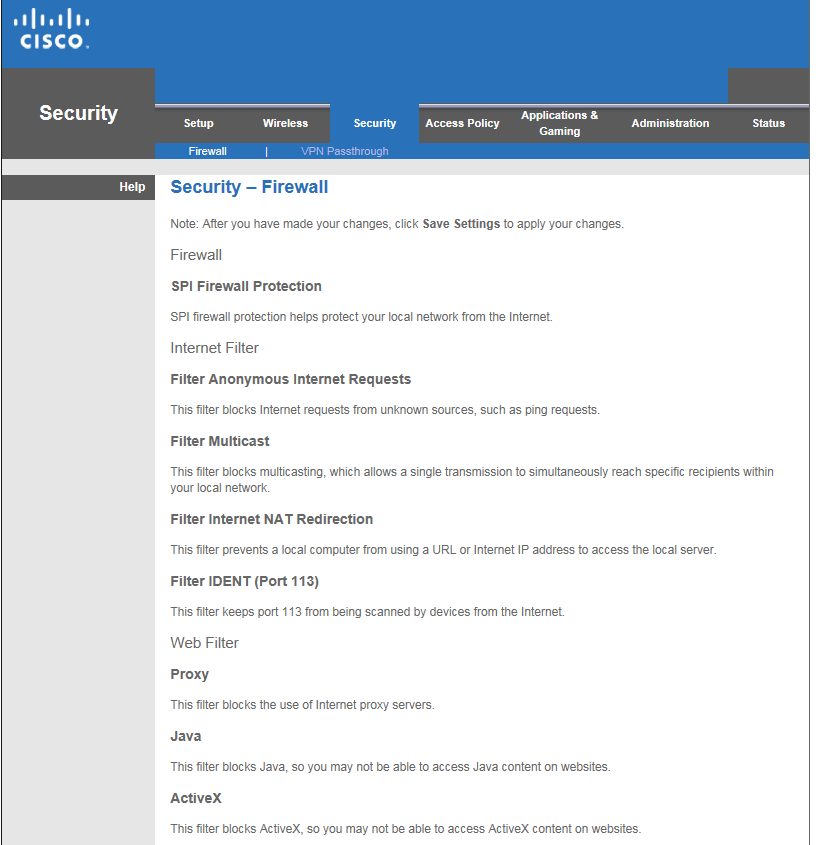
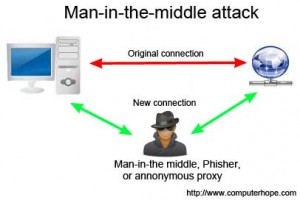 One of the best ways to prevent physical devices on the network from being hacked is to prevent access to them. Securing routers and modems in areas that are open to the public will prevent someone from tampering with them. Additionally, enforcing controlled access to network rooms helps prevent man-in-the middle attacks. Controlled access should apply to the server room, as well, to prevent someone from plugging in a USB with malicious programs, or uploading a virus directly to the server.
One of the best ways to prevent physical devices on the network from being hacked is to prevent access to them. Securing routers and modems in areas that are open to the public will prevent someone from tampering with them. Additionally, enforcing controlled access to network rooms helps prevent man-in-the middle attacks. Controlled access should apply to the server room, as well, to prevent someone from plugging in a USB with malicious programs, or uploading a virus directly to the server.
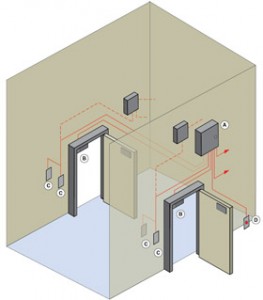 However, having a secured entry to locations has its weakness, too — mostly unintentional, human error. The most common mistake is kindness to other people. This sounds bad, I know, but it can be dangerous to hold a door for someone. Or to let in someone in who forgot his/her key card. The bad guys will try to play on the kindness of others. There is also tailgating — when someone with access to an area opens the door, and then another person catches the door before it closes. This is one way criminals gain access to secured areas without the necessary credentials. The best protection against tailgating is a mantrap (no, we are not talking about Indiana Jones-type traps). A mantrap is created when you have to go through two doors to access the secure room, preferably with a hallway between the two doors. This method traps the tailgater in-between the two doors and helps prevent access to the secure area.
However, having a secured entry to locations has its weakness, too — mostly unintentional, human error. The most common mistake is kindness to other people. This sounds bad, I know, but it can be dangerous to hold a door for someone. Or to let in someone in who forgot his/her key card. The bad guys will try to play on the kindness of others. There is also tailgating — when someone with access to an area opens the door, and then another person catches the door before it closes. This is one way criminals gain access to secured areas without the necessary credentials. The best protection against tailgating is a mantrap (no, we are not talking about Indiana Jones-type traps). A mantrap is created when you have to go through two doors to access the secure room, preferably with a hallway between the two doors. This method traps the tailgater in-between the two doors and helps prevent access to the secure area.
These are easy ways you can help prevent physical devices from being tampered with. And your network from being hacked. If you have any questions, or would like to discuss further security options for your company, please give us a call at 888-244-1748. Or email us at [email protected]. We’re here for you 24/7, 365.